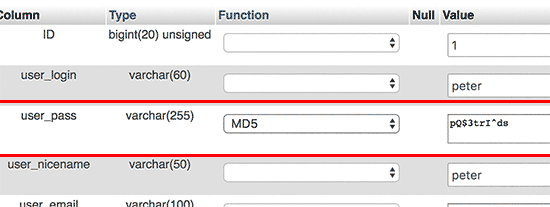
Very useful tip from this post:
http://www.wpbeginner.com/beginners-guide/how-to-reset-a-wordpress-password-from-phpmyadmin/
Thank you!

What's new in web design and development – Principal: Paul D. Gurney.
Very useful tip from this post:
http://www.wpbeginner.com/beginners-guide/how-to-reset-a-wordpress-password-from-phpmyadmin/
Thank you!

One more attack vector to be thinking about!
From a security perspective, Unicode domains can be problematic because many Unicode characters are difficult to distinguish from common ASCII characters. It is possible to register domains such as “xn--pple-43d.com”, which is equivalent to “аpple.com”. It may not be obvious at first glance, but “аpple.com” uses the Cyrillic “а” (U+0430) rather than the ASCII “a” (U+0041). This is known as a homograph attack.
Chrome 59 will protect you from these phishing attempts by converting the maliciously-similar name to the Punycode version, thus making you aware of something amiss.
Firefox users can limit their exposure by going to about:config and settingnetwork.IDN_show_punycode to true. This will force Firefox to always display IDN domains in its Punycode form, making it possible to identify malicious domains. Thanks to /u/MARKZILLA on reddit for this solution.
Thus, the attack form of apple.com will show as https://www.xn--80ak6aa92e.com
On Twitter @Xudong_Zheng says a simple way to limit the risk from bugs such as this is to always use a password manager, which can identify that the similar letters are not the same.
October 2014 brought with it a new cyber-attack method to the Internet: POODLE, the ‘Padding Oracle On Downgraded Legacy Encryption’ attack. The attack is against the SSLv3 protocol, which powers the HTTPS secure browsing system we’re all used to.
What can you do?
1. Check your browser:
https://dev.ssllabs.com/ssltest/viewMyClient.html
Then disable SSLv3 support in your browser(s):
https://scotthelme.co.uk/sslv3-goes-to-the-dogs-poodle-kills-off-protocol/
Firefox was the easiest to change. Safari has no known fix yet, and Mac Chrome requires a command line tweak to modify. Even the Chrome Canary build is still vulnerable.
2. Check to see if your web server is vulnerable:
https://www.tinfoilsecurity.com/poodle
Then ask your hosting company to disable SSLv3 on the server:
https://scotthelme.co.uk/sslv3-goes-to-the-dogs-poodle-kills-off-protocol/
From ArsTechnica:
There is an easy test to determine if a Linux or Unix system is vulnerable. To check your system, from a command line, type:
env x='() { :;}; echo vulnerable' bash -c "echo this is a test"
If the system is vulnerable, the output will be:
vulnerable
this is a test
An unaffected (or patched) system will output:
bash: warning: x: ignoring function definition attempt
bash: error importing function definition for `x'
this is a test
The fix is an update to a patched version of the Bash shell. To be safe, administrators should do a blanket update of their versions of Bash in any case.
A computer security firm called Norse
has released a stunning data visualization map of internet attacks. It shows a fraction of the scope of constant threats affecting countries today. You can see penetration attempts in real time over services like http (web servers) and smtp (email servers), and more.
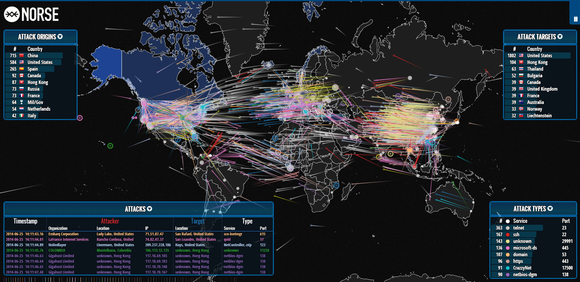
via PC World from this article.
Visit this site: https://lastpass.com/heartbleed/
to verify if any website is still vulnerable to the bug. (Remember, not all websites used the same OpenSSL protocol.)
On April 8 I was notified by WiredTree, our hosting company, that their servers had been patched against a newly discovered (and serious) flaw in the SSL encryption technology which underpins secure browsing over https.
It is called the Heartbleed bug.
Our servers were not affected, as they ran CentOS5 and did not use Litespeed. Other sites which did use LiteSpeed were affected.
Read more at:
http://heartbleed.com/
https://blog.cloudflare.com/staying-ahead-of-openssl-vulnerabilities
UPDATE
An article on Thursday explains how the bug crept in the Open Source software.
Heartbleed, a “catastrophic” security flaw in the OpenSSL cryptographic protocol that has affected two-thirds of the entire Internet’s communications, was committed at 10:59 pm on New Year’s Eve by Seggelmann, a 31-year-old Münster, Germany-based programmer.
That night, he made an error that has been compared to the misspelling of Mississippi, a careless but almost inevitable mistake that went undetected for over two years.
This article on 10 things you MUST know before you register a domain name with anyone
is useful: http://www.domainwarning.com
That’s why we recommend Hover.com for domain name purchases.
If you have a blog, you need to install this plug-in immediately.
http://wordpress.org/extend/plugins/limit-login-attempts/
There is currently a major type of internet attack being waged by botnets against webservers running WordPress. These bots brute-force their way in past your password screen by making thousands of guesses until they gain entry. WordPress currently does not limit the number of incorrect password attempts. Until it does, you need a plug-in that provides the limiting.
There is currently a significant attack being launched at a large number of WordPress blogs across the Internet. The attacker is brute force attacking the WordPress administrative portals, using the username “admin” and trying thousands of passwords. It appears a botnet is being used to launch the attack and more than tens of thousands of unique IP addresses have been recorded attempting to hack WordPress installs.
One of the concerns of an attack like this is that the attacker is using a relatively weak botnet of home PCs in order to build a much larger botnet of beefy servers in preparation for a future attack. These larger machines can cause much more damage in DDoS attacks because the servers have large network connections and are capable of generating significant amounts of traffic. This is a similar tactic that was used to build the so-called itsoknoproblembro/Brobot botnet which, in the Fall of 2012, was behind the large attacks on US financial institutions.
Source: http://blog.cloudflare.com/patching-the-internet-fixing-the-wordpress-br
Wired has been discussing an emerging email security vulnerability this month.
The problem lies with DKIM keys (DomainKeys Identified Mail). DKIM involves a cryptographic key that domains use to sign e-mail originating from them — or passing through them — to validate to a recipient that the domain in the header information on an e-mail is correct and that the correspondence indeed came from the stated domain. When e-mail arrives at its destination, the receiving server can look up the public key through the sender’s DNS records and verify the validity of the signature.
Learn more from the article, and ask your hosting company if they use strong — 1024-bit — DKIM. Why?
A hacker who cracks a DKIM key can use it to send out phishing attacks to victims to trick them into believing that a fake e-mail is actually a legitimate e-mail from their bank or another trusted party. Such phishing attacks can be used to trick users into handing over the login credentials to their bank or e-mail account.