Very useful tip from this post:
http://www.wpbeginner.com/beginners-guide/how-to-reset-a-wordpress-password-from-phpmyadmin/
Thank you!

What's new in web design and development – Principal: Paul D. Gurney.
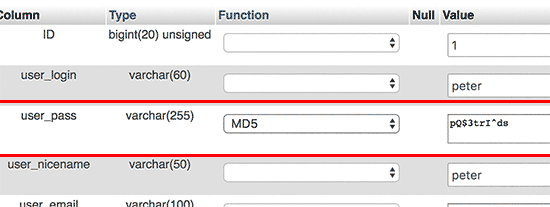
Very useful tip from this post:
http://www.wpbeginner.com/beginners-guide/how-to-reset-a-wordpress-password-from-phpmyadmin/
Thank you!

One more attack vector to be thinking about!
From a security perspective, Unicode domains can be problematic because many Unicode characters are difficult to distinguish from common ASCII characters. It is possible to register domains such as “xn--pple-43d.com”, which is equivalent to “аpple.com”. It may not be obvious at first glance, but “аpple.com” uses the Cyrillic “а” (U+0430) rather than the ASCII “a” (U+0041). This is known as a homograph attack.
Chrome 59 will protect you from these phishing attempts by converting the maliciously-similar name to the Punycode version, thus making you aware of something amiss.
Firefox users can limit their exposure by going to about:config and settingnetwork.IDN_show_punycode to true. This will force Firefox to always display IDN domains in its Punycode form, making it possible to identify malicious domains. Thanks to /u/MARKZILLA on reddit for this solution.
Thus, the attack form of apple.com will show as https://www.xn--80ak6aa92e.com
On Twitter @Xudong_Zheng says a simple way to limit the risk from bugs such as this is to always use a password manager, which can identify that the similar letters are not the same.
Classic article from Jeff Atwood in 2008 at Coding Horror:
I’ve often thought that software developers were akin to Magpies, birds notorious for stealing shiny items to decorate their complex nests. Like Magpies, software developers are unusually smart and curious creatures, almost by definition. But we are too easily distracted by shiny new toys and playthings.
Jeff added: I became a programmer because I love computers, and to love computers, you must love change. And I do. But I think the magpie developer sometimes loves change to the detriment of his own craft.
Jeff is the programmer who created Stack Overflow and Discourse.
Perhaps a better way for a “tech neophyte” to try out coding is to learn how to write HTML/CSS. This pairing is far more self-contained and visual, and gratifying, than programming initially is (no matter the flavor, whether JS, Python, Swift, they all are far more complex with abstract logic).
Learning how to create a static web page only requires a layout, a text editor and a browser. You can try your hand at building a magazine page, for example, with its masthead, article areas and footer—and you will not be dealing with math or abstract problem solving that coding soon requires.
The learner can see how the basic HTML language syntax works (e.g. simple tags go around the words to style or structure them)… experience how the browser is strict about typos (early experience in debugging!); see how dependencies are linked in (graphics, external hyperlinks); see how the classes and IDs from the CSS file influence the HTML elements; and so on.
If the somewhat tedium of composing blocks of HTML and CSS code is gratifying to the learner, and it sparks an interest, then they can continue gaining fluency in the constructs and begin to appreciate how WYSIWYG editors work (like in WordPress or BigCommerce, say). This can be so helpful for business owners or bloggers, to fix the mistakes that RTEs can introduce from copy/paste actions from other sources (ie. Word pastes).
So, I’m proposing that fluency in HTML is a more basic, essential skill for today’s professionals than actual coding.
From an excellent Ars Technica article: Choosing between MySQL and NoSQL.
http://arstechnica.com/information-technology/2016/03/to-sql-or-nosql-thats-the-database-question/
“For 30 years in the IT industry, we’ve had traditional development models,” Gnau said. “We grab users, put them in a room, get their requirements, build out the design, look for data to find structures and reporting, implement and hand it back to users. It was a traditional waterfall approach. Even agile development starts with requirements and winds up with results.
“In Hadoop, you need to challenge that and turn it around. Data is not structured. Users may not know what the requirements are. It’s an inverse process—you land the data, find data scientists to find relationships that are interesting and appealing, and turn that into requirements that yield a system. It’s the opposite approach to a traditional process.”
On April 8 I was notified by WiredTree, our hosting company, that their servers had been patched against a newly discovered (and serious) flaw in the SSL encryption technology which underpins secure browsing over https.
It is called the Heartbleed bug.
Our servers were not affected, as they ran CentOS5 and did not use Litespeed. Other sites which did use LiteSpeed were affected.
Read more at:
http://heartbleed.com/
https://blog.cloudflare.com/staying-ahead-of-openssl-vulnerabilities
UPDATE
An article on Thursday explains how the bug crept in the Open Source software.
Heartbleed, a “catastrophic” security flaw in the OpenSSL cryptographic protocol that has affected two-thirds of the entire Internet’s communications, was committed at 10:59 pm on New Year’s Eve by Seggelmann, a 31-year-old Münster, Germany-based programmer.
That night, he made an error that has been compared to the misspelling of Mississippi, a careless but almost inevitable mistake that went undetected for over two years.
I was searching for an Add-On to Thunderbird v24 that would batch-add all the message’s recipients to a new Contact Group.
Gina at LifeHacker pointed out a good one. And the developer’s site is here: http://addresscontext.mozdev.org/index.html
But it is incompatible with the latest version of Thunderbird. Please update it, Mike.
If you need this too, email the author:
mikekrieger [at] gmail [dot] com
Gmail removes the entire HEAD portion of your email’s HTML. It will also remove any STYLE elements. However, you can easily overcome this limitation by inlining your CSS using one of many online tools:
MailChimp’s CSS Inliner
TorchBox Apps Inliner Styler
MailerMailer Magic CSS Inliner Tool
Great article about risks of free wordpress themes found in the wild…
http://wpmu.org/why-you-should-never-search-for-free-wordpress-themes-in-google-or-anywhere-else/
A few months ago I wrote about WordPress Security. Now, armed with … builtBackwards’ Theme Authenticity Checker Plugin and Donncha O Caoimh’s Exploit Scanner, I’m going to take a look through the first page of Google to see just how safe pages ranking for “Free WordPress Themes” are.